Tips: On-screen trail solution Ilegal View whitelisting function works against cyber-attack very effectively.
Today's topic is how screen trail, log trail software, Illegal View can contribute to create your strong end-point security system with whitelisting function.
Whitelist is simple but very strong end-point security solution, with which only approved applications can be registered and used in PCs in your network system. If some application is not approved one, it does not allow to boot up without exception. Thus, even if computer virus breaks into your IT system, it prohibits to boot up and thus protect your IT system.
It is very effective method against back door attack, fake log in, virus infection and fake program.
Illegal View has Whitelist function deployed as a standard function.
- It allows to register approved soft wares automatically.
- Even if computer virus breaks into the system for some reason, Illegal View whitelist function blocks harmful applications from booting up. It means that your IT system are safe and protected.
- Illegal View issues a notice to administrator automatically whenever problem occurs and disables corresponding PC to avoid further infection and information leakage.
Also, administrator can best utilize screen audit trail and log audit trail for investigating troubles if any and immediately implement countermeasures for solving problem.
The whitelisting is easy and simple with Illegal View.
- Prepare a master PC which has only approved applications. if you have several groups or units which require different application configuration, then please be ready to have master PCs for each group or unit.. And then, all applications are once booted up before proceeding to step 2. This initial set up is the very key for successful whitelisting.
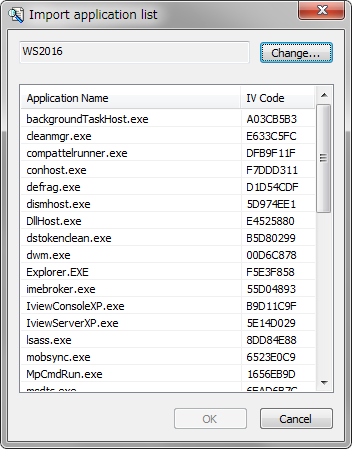
- Implement whitelisting function. With this step, only approved applications are registered and becomes bootable.
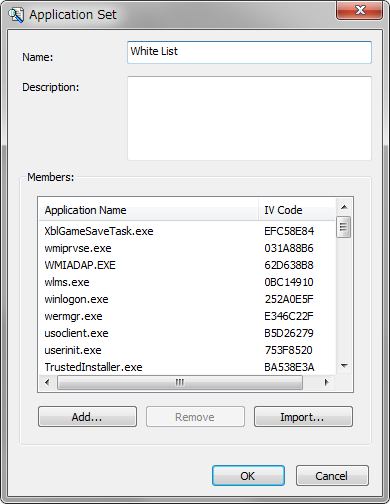
- Illegal View auto distribution function allows to distribute and install only approved and registered applications of master PC to end user PCs of the same group.
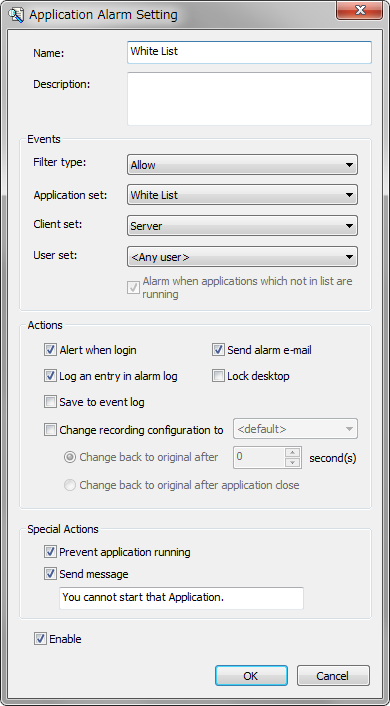
If user PC has already installed non approved applications, Whitelisting function does not allow to boot up such applications. Furthermore, auto distribution does not interfere your daily business activities at all.
These simple and easy 3 steps are all required for activating whitelisting function with Illegal View. With automatic registration function and auto distribution function, you can create strong cyber attack defense infrastructure in your IT system.
The detailed whitelisting information is available with PDF format for Illegal View users. Please feel free for information by using contact form of our home page.
Illegal View is well known as screen trail and operation trail solution. Actually, however, it is a strong end -point security system as explained with Illegal View whitelist function.
We are very happy if we can be of your help to best utilize Illegal View full functions for establishing strong IT security infrastructure of your company.
IT Fraud Monitoring, Cyber-Attack Defense, Endpoint Security: Illegal View
