Illegal View ( Professional Version )
Overview
What is Illegal View?
Illegal View is a security software for Windows developed with KDTS's proprietary technology. Thus, it has quite a unique feature of recording on-screen activities of user session at a very minimum network load and record data size. It also has a versatile feature to keep track of all user activities of user session and thus we call it "on-screen activity trail solution" and "operation trail solution."
KDTS has now released PCI DSS encryption version Illegal View for PCI DSS for business entities seeking for accreditation of PCI DSS.
Recording on-screen activities of user session prevents user from having improper, unauthorized system operations as user knows that unauthorized operation is monitored and recorded. Recorded picture can effectively be used for quick and prompt incident investigation, as well as audit trail and non-fraud evidence.
It also has a versatile feature such as RDP, strong search and retrieval functions, various alert functions, user protection functions such as Whitelist, Blacklist, USB use control.
Thus, it is also an end-point security solution which protects user and your company's IT infrastructure from cyber-attack and internal fraud operation.
User can best utilize Illegal View for the following situations;
- Prevention of fraudulent operation of IT system
- Audit trail and non-fraud evidence
- Real-time monitoring
- End-point security solution against cyber-attack
- Training utilizing recorded on-screen picture
- Work style reform
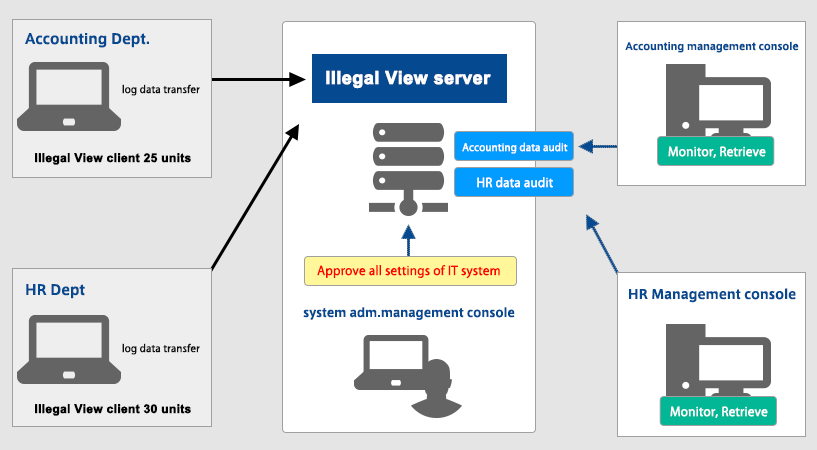
Illegal View typical deployment case
Main Features
Illegal View is an "on-screen activity trail solution", "operation trail solution", and "end-point security solution" developed with kdts's proprietary technology.
It has a versatile feature such as real-time monitoring, search and retrieval function, various alert setting functions, user protection functions and thus it protects your company from internal improper operation and cyber-attack from outside.
Feature details
Illegal View is an "on-screen activity trail solutions", "operation trail solution", "end-point security solution" for Windows developed with KDTS's proprietary technology.
Illegal View is an "on-screen activity trail solutions", "operation trail solution.", "end-point security solution" for Windows developed with KDTS's proprietary technology. It is a software 100% made in Japan, therefore kdts can offer quick and prompt response to user requests and requirements.
Picture can be recorded from 0.5 seconds and is encrypted.
24hours and 365 days continuous recording and off-line recording are possible.
Or,user can record only selected on-screen session based on pre-set conditions
With this time version up, new feature of recording operator picture all the time with built-in camera or with USB attachable camra is now available.
With KDTS's proprietary technology, huge recorded data are compressed to a minimum level, enabling network load to be at the very minimum.
Storage data size is at a minimum level as well due to the same reason above.
Moreover, all the data are encrypted and cannot be decoded.
One server can control more than 5000 user sessions.
(Recommended: multi-core (above quad core) CPU with 16 giga bite or more memory server use machine)
With this unique feature, user can easily introduce Illegal View into system any time, as it is not necessary to upgrade or alter current network and hardware infrastructure.
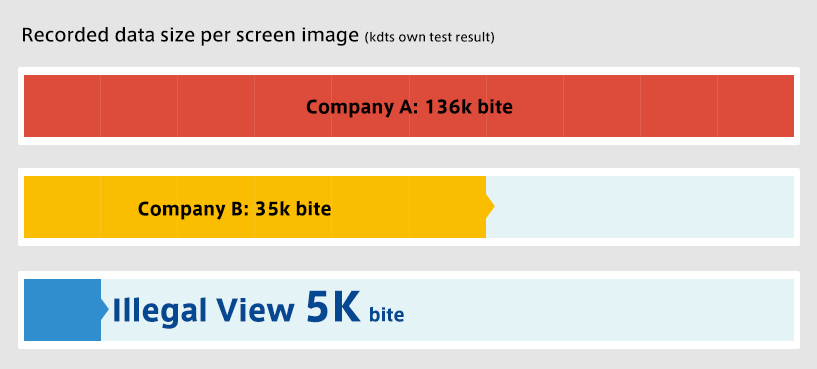
Illegal View high image compression requires very small HDD capacity (Data is recorded with the following screen image conditions; 1024x768/5 sec interval/ 8 hours/ 16 colors)
RDT feature
Illegal View can record RDP sessions and operation activity of remote PCs with no Illegal View agent installed. (XenApp environment is also applicable.)
- It records not only on-screen picture but also all kinds of operation logs such as text, file access, key and mouse stroke, resource, and application.
- In case of springboard server deployed, RDP connection can record on-screen sessions only. But if Illegal View agent is installed to springboard server, it can record all kinds of operation logs as well.
- On-screen picture data and log data are all encrypted and impossible to decode. Only authorized user is allowed to monitor the recorded data and no one else.
Illegal View System case with Springboard server deployed
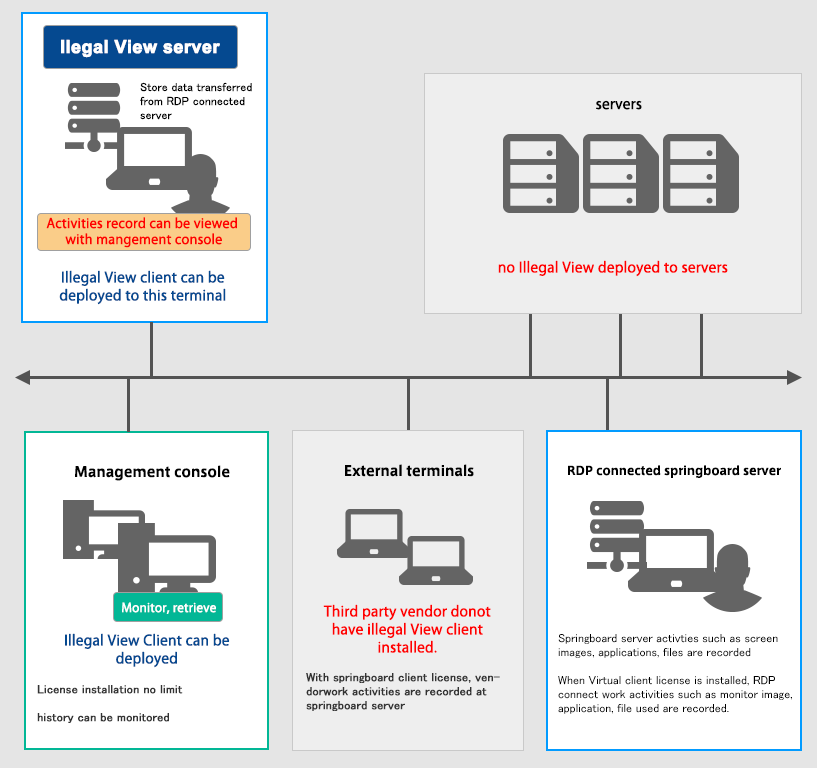
- Server license : 1 server license with free management console license
- Client license: the number of license is up to the number of springboard servers monitored
- Virtual client license:the number of license required is up to the number of simultaneously connected pringboard servers
- This license is requqired for RDP session recording
- The number of RDP session per springboard server cannot be identified and so maximum number of license are required.
- No installation to terminal is needed. When the terminal with Illegal View Client is RDP connected, the number of license is counted based on the number of terminal simultaneously connected up to the number of license purchased.
Illegal View license is applicable for any server OS/Client OS/ 32bitOS/64bitOS.
Illegal View system case with Client license deployed to each server
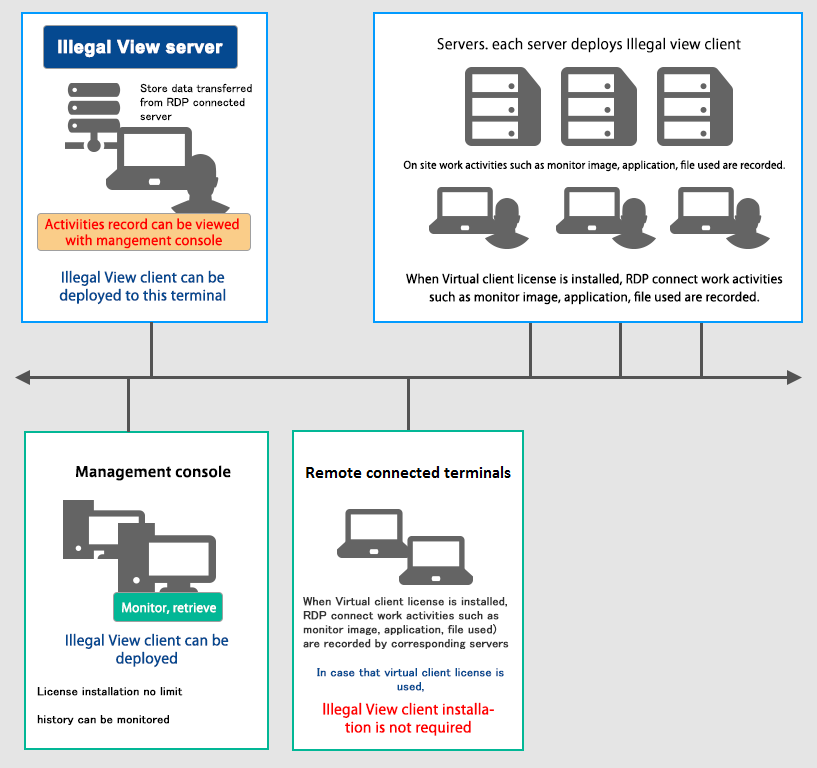
- Server license : 1 server license with free management console license
- Client license: the number of license is up to the number of springboard servers monitored
- Virtual client license:the number of license required is up to the number of simultaneously connected pringboard servers
- This license is requqired for RDP session recording
- The number of RDP session per springboard server cannot be identified and so maximum number of license are required.
- No installation to terminal is needed. When the terminal with Illegal View Client is RDP connected, the number of licens is counted based on the number of terminal simultaneously connected up to the number of license purchased.
Illegal View license is applicable for any server OS/Client OS/ 32bitOS/64bitOS.
Various powerful functions
Real-time monitoring feature
Illegal View allows administrator to monitor user operations in real-time, as well as monitoring multi-users operations in real-time simultaneously.
When improper operation or mal-function of system is detected, administrator can issue alert message to user in real-time and, if necessary, make the end user terminal inoperative.
Powerful search retrieval feature and alert feature
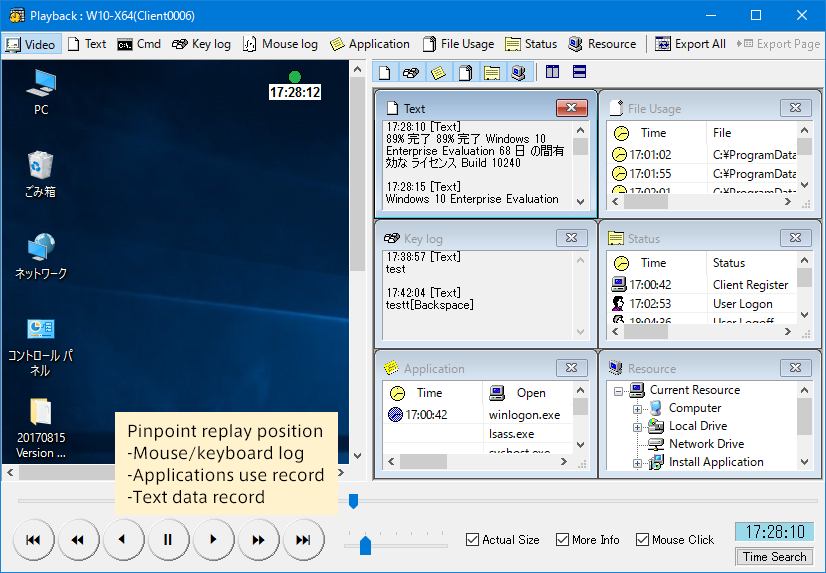
Illegal View can record not only monitoring screen picture but also text log, command log, keyboard stroke, application log, file usage log, status log and resource log. Powerful search and retrieval function allow to search various kinds of logs and retrieve on-screen pictures you need to review quickly and promptly.
At the same time, administrator can configure alert-setting so that alert is to be issued automatically whenever the conditions are met.
Enhanced end-point security features
Illegal View has versatile enhanced end security features.
It blocks unauthorized use of important files data and USB by inside user, preventing leakage of important data.
It can also set up whitelist and blacklist and to protect end user from cyber-attack from outside. Please note that whitelisting is simple and easy with Illegal View.
It does block booting up of malware program even when the malware program penetrates into your IT system.
For further details, please review the following Tips blog about easy and simple setting of Illegal View whitelisting.
Non- invalidation features
Illegal View equips observer function, stealth function and firewall countermeasure function so that it ensures recording data 24 hours and 365 days without any interruption. Illegal View cannot be invalidated whatsoever.
PCI DSS encryption version Illegal View is available
Illegal View adopts kdts proprietry encryption technology and thus the end user data security is 100% protected. This time, in response to our user's requests, we have adopted PCI DSS encryption method and developed PCI DSS version Illegal View. Accordingly, those who are seeking for accreditation of PCI DSS can make use of PCI DSS version Illegal view.
The PCI DSS specifies 12 requirements for compliance, orgainzed into 6 logically related groups called "control objectives".
Illegal View can be utilized for assisting to meet requirements 2, 3, 6, 7, 8 and 10.
Illegal View Page List
- About Illegal View
- Functionality and System Requirement
- Collaboration
