SPIDER
OVERVIEW
SPIDER is a software specifically designed to manage privileged ID user and regular ID user activity.
Privileged ID user has all mighty authority to manage IT system and SPIDER ensures and validates that privileged ID user can exercise its authority to manage IT system properly and rightfully.
SPIDER is developed only with KDTS's proprietary technology. It is a unique agentless monitoring solution for privileged ID user and regular ID user activity.
SPIDER manages activity monitoring via WEB and therefore, it has a minimum network load.
SPIDER can be applicable for not only Windows environment but also Linux. Furthermore, it works in thin client environment and VDI environment.
SPIDER has a direct log-in control feature and it controls application for approval, approval confirmation, ID management and access management.
SPIDER server automatically validates all ID data registered in high-speed whether they are rightful IDs or not. Thus, it ensures that ID management is flawless all the time.
SPIDER is an ideal solution for managing large scale privileged ID user and regular ID user activity.
SPIDER is specifically designed to manage ID user activity . With Illegal View linkage, you can record not only ID user activity but also activity contents with recorded on-screen image and various logs such as text, access record and others.
Thus, the linkage between SPIDER and Illegal View ensures that IT system is flawless from the viewpoint of ID management and audit trail of privileged user activity.
Main Feature
SPIDER is a software specifically designed to manage privileged ID user and regular ID user activity. SPIDER is developed only with KDTS's proprietary technology and it is a unique agentless monitoring solution for privileged ID user and regular ID user activity.
The below is the comparison table among privileged ID management and software currently available. You can find that SPIDER is the most reliable, flawless management solution for privileged ID and regular ID in the market.
Privileged ID Management system comparison list
| Method | Mechanism | Module | system reliability | Anti-spoofing | Issue / weak point |
|---|---|---|---|---|---|
| Gate type | Program gate type | required | ★★☆☆☆ | ★★☆☆☆ | if authentic ID is used, spoofing cannot be detected |
| Gate type | Gateway control type | not required | ★★★☆☆ | ★★☆☆☆ | if authentic ID is used, spoofing cannot be detected. Also, Gateway setting change may cause authorized registered ID inoperative |
| Log in control type | re-write log in module | required | ★★☆☆☆ | ★★★★☆ | if certification is deluded somehow, log in is allowed with standard OS |
| SPIDER direct log in control type | remote control type | not required | ★★★★☆ | ★★★★★ |
No module makes no effect to current IT system and yet can monitor, report ID use status and detect and stop unauthorized ID use |
SPIDER requires a server and nothing else. ID information is encrypted and connected to WEB. Therefore, there is no network load to company IT system.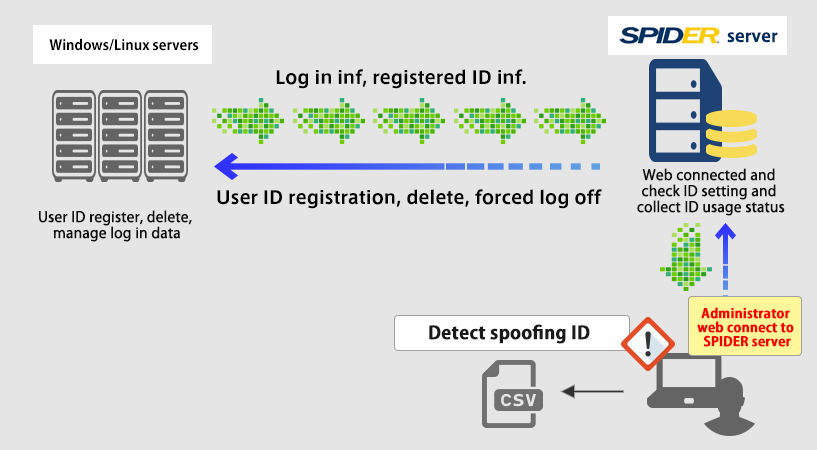
Ideal solution for large scale ID user management
SPIDER is designed to manage up to 50,000 PCs and 10,000 users with one server. And yet, network load to your IT system remains at a very minimum level.
Applicable to various user IT environment
SPIDER can be deployed under not only Windows but also Linux environment. Furthermore, it also works under thin client and VDI environment. It also works under non-domain and non-active directory environment.
Easy operation for managing privileged ID user and regular user activity
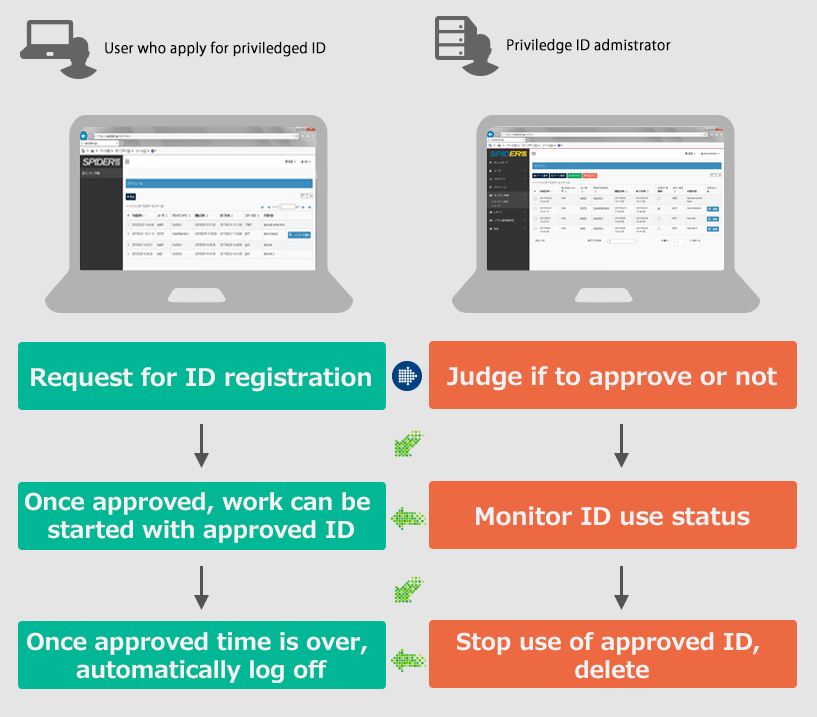
SPIDER has a work flow function for application for approval, approval permission. It also can designate expiration date setting of privileged ID and manage access control.
Work flow chart from application till finish of activity using approved ID
High-speed registered ID data validation function
SPIDER has a built-in automatic ID validation function and the validation can be done with high-speed. Thus, ID information in the system is always clean and flawless. Even if invalid ID or fake ID is created and used in the system, SPIDER can detect and nullify it instantly. User using such ID is instantly forced to shut down the operation.
SPIDER can scan and validate all ID data with the speed of 50 units per minute according to our test results
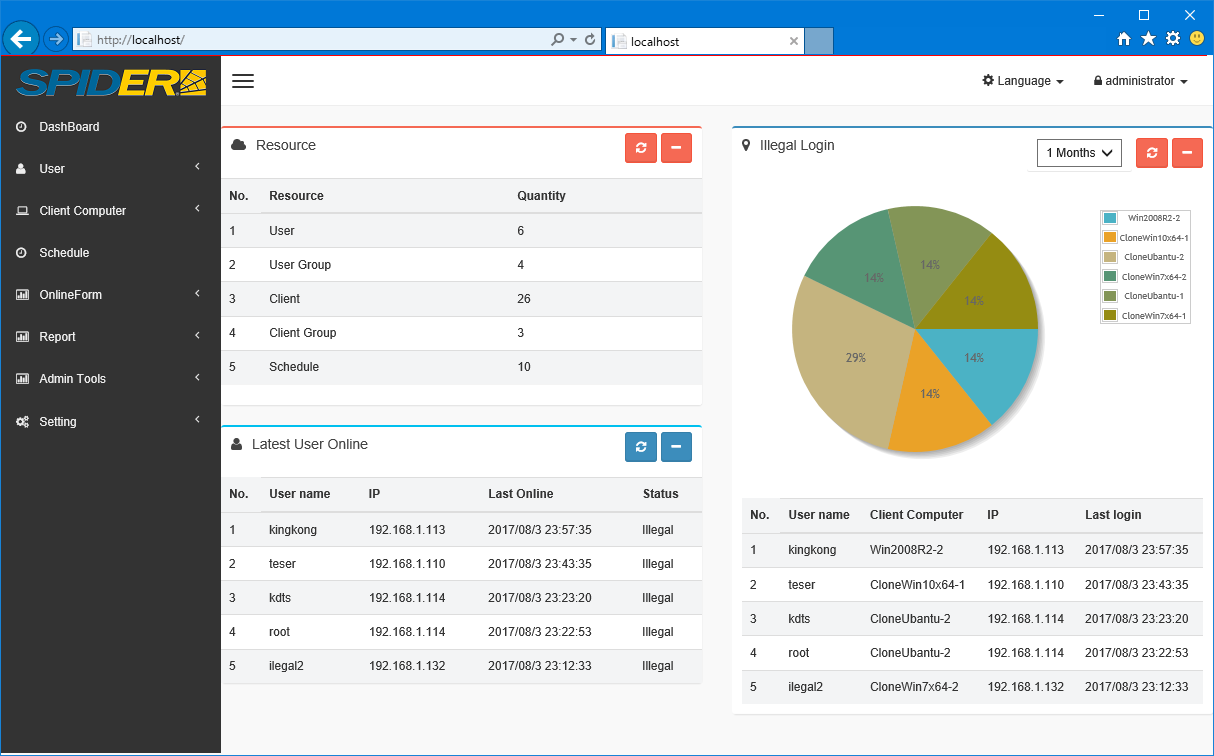
Dashboard function allows to view privileged user ID and regular user ID activity status and history at a glance.
Unauthorized access data, registered resource by category, user history can be glanced over with dashboard anytime. Easy to monitor ID management status.
See Sample image
Audit trail and reports
SPIDER can create following PDF data for audit trail.
- schedule
- login and logout
- registered user information
- registered client
- user group list
- client group
SPIDER Page List
- About SPIDER
- Functionality and System Requirement
- Collaboration
